Windows Server Active Directory upgrades are a part of administering Windows Server Active Directory infrastructure on-premises. Currently, businesses may have a mix of Windows Server infrastructure and many are running Windows Server 2019 domain controllers in their environment which currently offer the latest and greatest features in the realm of Windows Server Active Directory infrastructure. As the release of Windows Server 2022 looms near on the horizon, many organizations will be looking at upgrading their existing infrastructure to include Windows Server 2022 on-premises Active Directory domain controllers. In this Windows Server Active Directory upgrade guide, we will look at the steps involved to upgrade Windows Server 2019 Active Directory to Windows Server 2022.
Windows Server 2022 features and Active Directory
Using the new capabilities and features unlocked by using Windows Admin Center, Windows Server 2022 will have the most direct integration with Azure of any server operating system. Microsoft is certainly wanting to get everyone focused on the Azure cloud. The new integrations with Azure make Windows Server 2022 an easy way that customers get a powerful on-premises operating system with all the Azure bells and whistles offered by Microsoft and unlocked potential with Windows Admin Center.
New Security features
One of the huge themes with Windows Server 2022 is security. Let’s face it. Security is on the minds of just about everyone these days, from IT operations, security engineers, and business leaders alike. Windows Server 2022 integrates the new Secured Core implementation from Microsoft. What is secured core? It is a new set of security features at the core of Windows Server 2022 and unlocked by the right hardware underneath the hood, such as TPM 2.0.
It also includes technologies such from current hardware OEM vendors including Bitlocker, and virtualization-based security (VBS) turned on by default. With the Secured Core server, these features are enabled out of the box from the OEM manufacturer so when the customer provisions the new hardware, a strong security foundation is enabled by default.
As this guide is focused on Windows Server 2022 Active Directory, as you can imagine, having even better security enabled for physical and virtual domain controllers is certainly a step in the right direction. Attackers are looking for easy ways to compromise Active Directory environments and user account in general. Having a better security foundation as provided in Windows Server 2022 helps businesses further protect Active Directory assets.
What about other Active Directory features found in Windows Server 2022? You are not going to notice a tremendously different Active Directory interface, experience, or capabilities with Windows Server 2022. Or, any differences at all. If you are like me, you have seen a trend from Microsoft of decoupling requirements of solutions from Active Directory proper, requiring domain joins, etc, for solutions to work correctly. Microsoft sees the writing on the wall with future infrastructure. Businesses will be stitching together infrastructure that exists in on-premises environments, cloud, and edge environments.
The traditional on-premises Active Directory that we have known now for decades is fading into the past as new solutions like Azure Active Directory (Azure AD) are more enticing with the tremendous focus on cloud and cloud-native applications. With remote work being the foreseeable future for most organizations, if not the permanent configuration for employees, traditional connectivity to on-premises infrastructure, including Active Directory domain controllers is no longer realistic. VPN connections for everyone is not considered feasible any longer and contains it own set of security vulnerabilities.Modern apps, containers, and Kubernetes
Another advancing area of focus and polishing from Microsoft is the area of containers, and specifically Kubernetes. Kubernetes is certainly where all the interest resides with containerized workloads. Kubernetes is by far the most powerful and popular container orchestration platform available. Windows Server 2022 will be able to use something known as group Managed Service Accounts (gMSAs) to provide an Active Directory identity to containers. You can do this today with domain-joined hosts, however, this will not be required with Windows Server 2022. Again, this goes back to the point of the traditional Active Directory requirements being phased out.
Upgrade Windows Server 2019 Active Directory to Windows Server 2022
So, let’s look at the process to upgrade Windows Server 2019 Active Directory to Windows Server 2022. For this run-through, I am using the Windows Server Insider Preview build 20344. What does this process look like? Well, actually not very different if at all than previous Windows versions. Here I am creating a new Windows Server 2022 VM in vSphere 7.0 Update 2. It is nice that we now have the Microsoft Windows Server 2022 option.
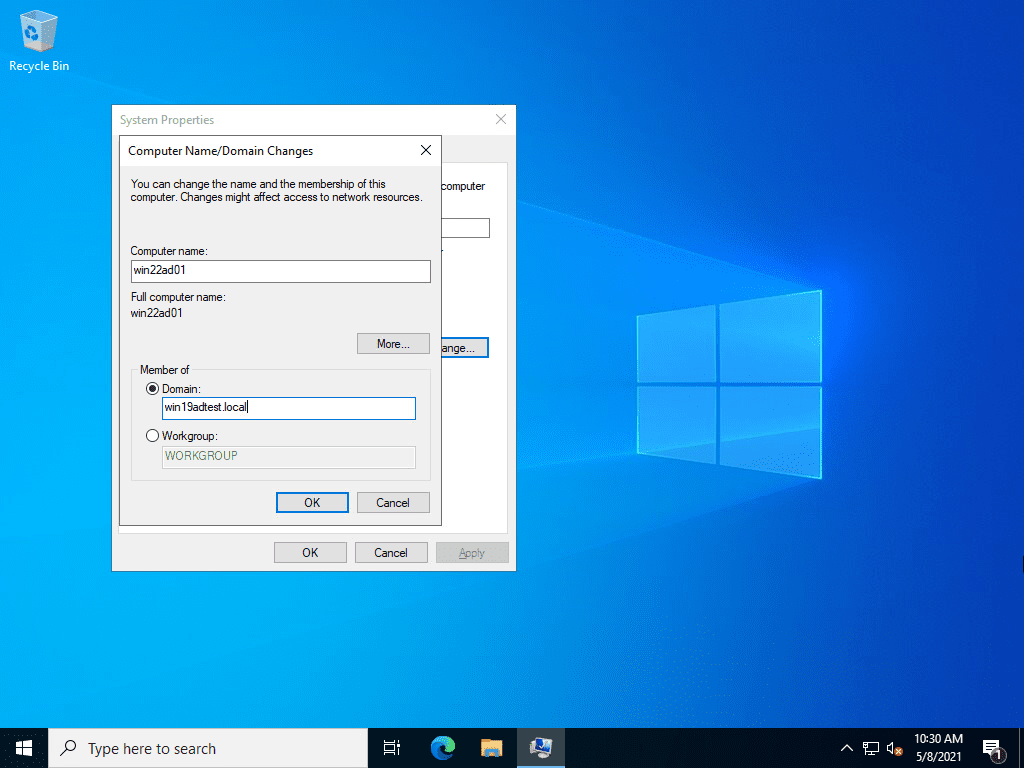
Here, I am joining the Windows Server 2022 server to the Windows Server 2019 Active Directory domain. This is being done after configuring the network on the Windows Server 2022 server for the domain, specifically DNS settings.
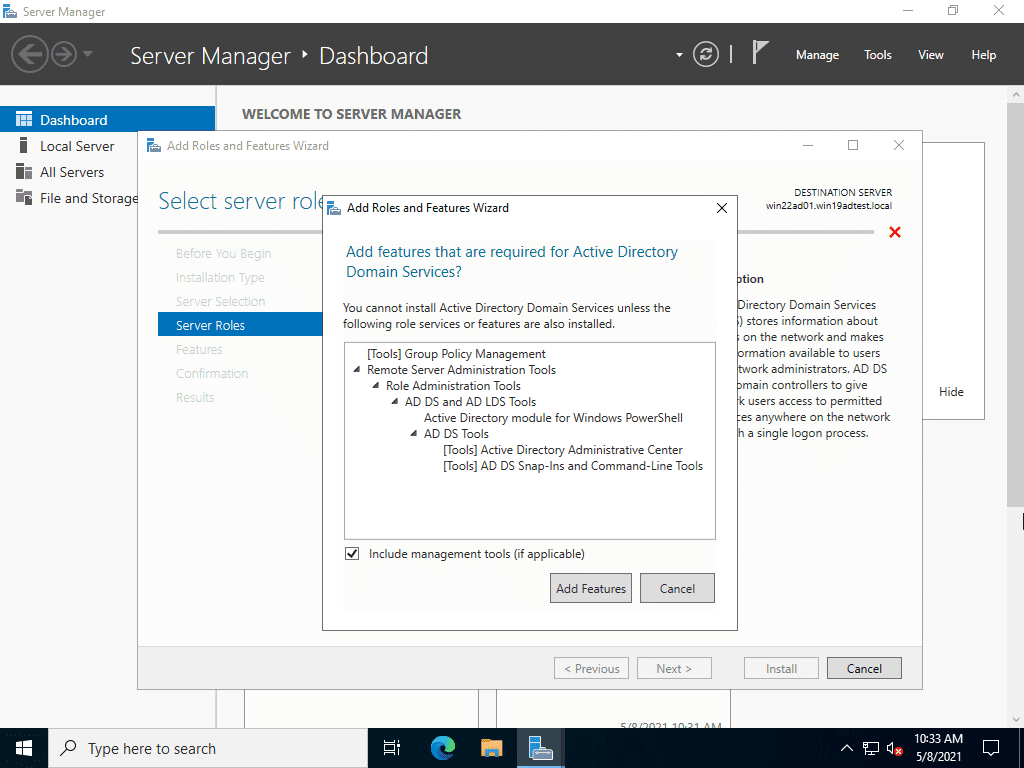
As you will see in the following screenshots, the process from Server Manager looks identical to Windows Server 2019. Here I am adding the Active Directory Domain Services (ADDS) role.
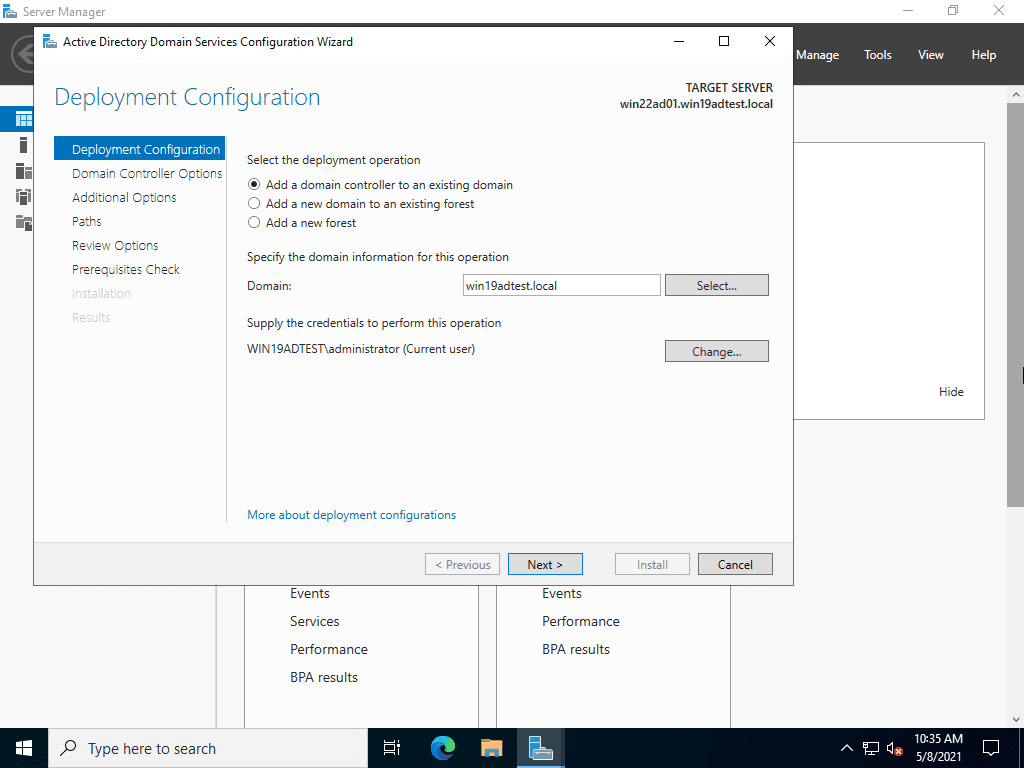
Below, I am selecting to Add a domain controller to an existing domain option and entering in the Windows Server 2019 domain.
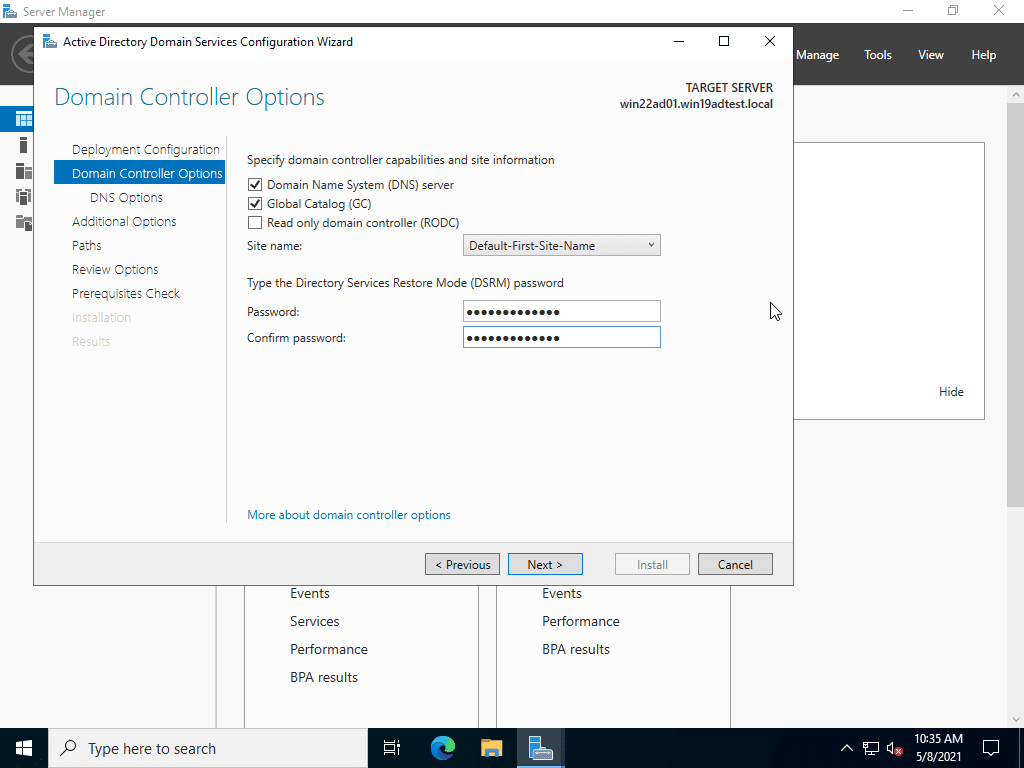
Next, select the domain controller capabilities and site information as well as configuring the DSRM password.
DNS options.
Choose the replication options, here leaving as the default all domain controller option.
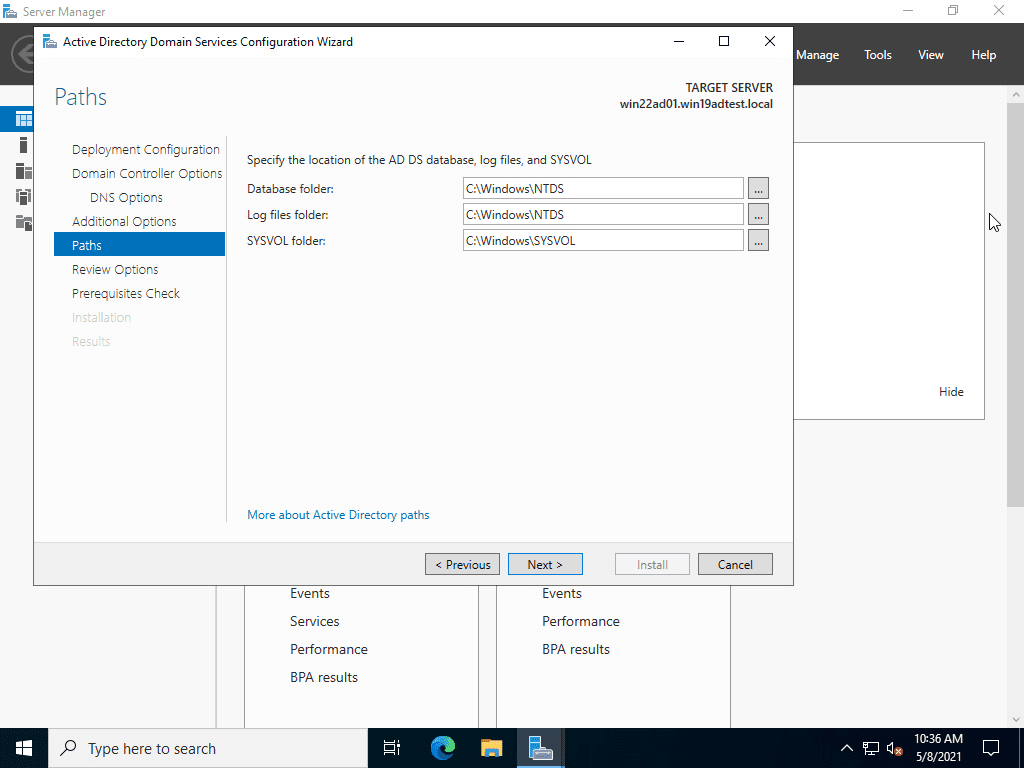
Specify the location of the AD DS database, log files and SYSVOL.
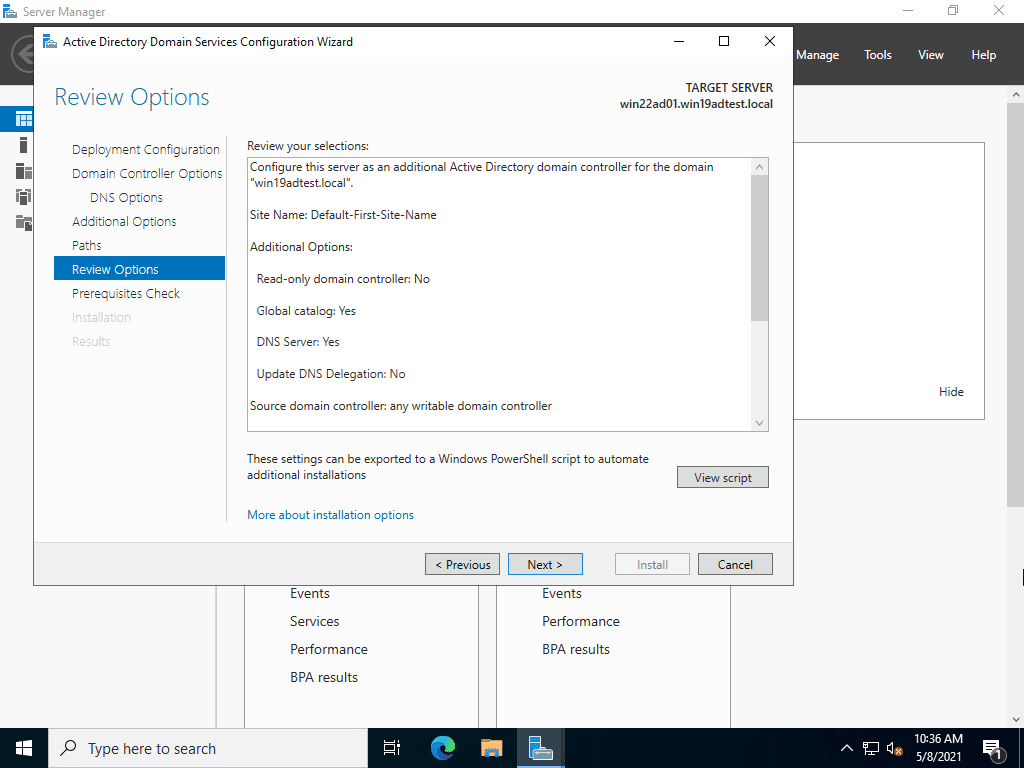
Review the options for the configuration of Active Directory on the Windows Server 2022 server.
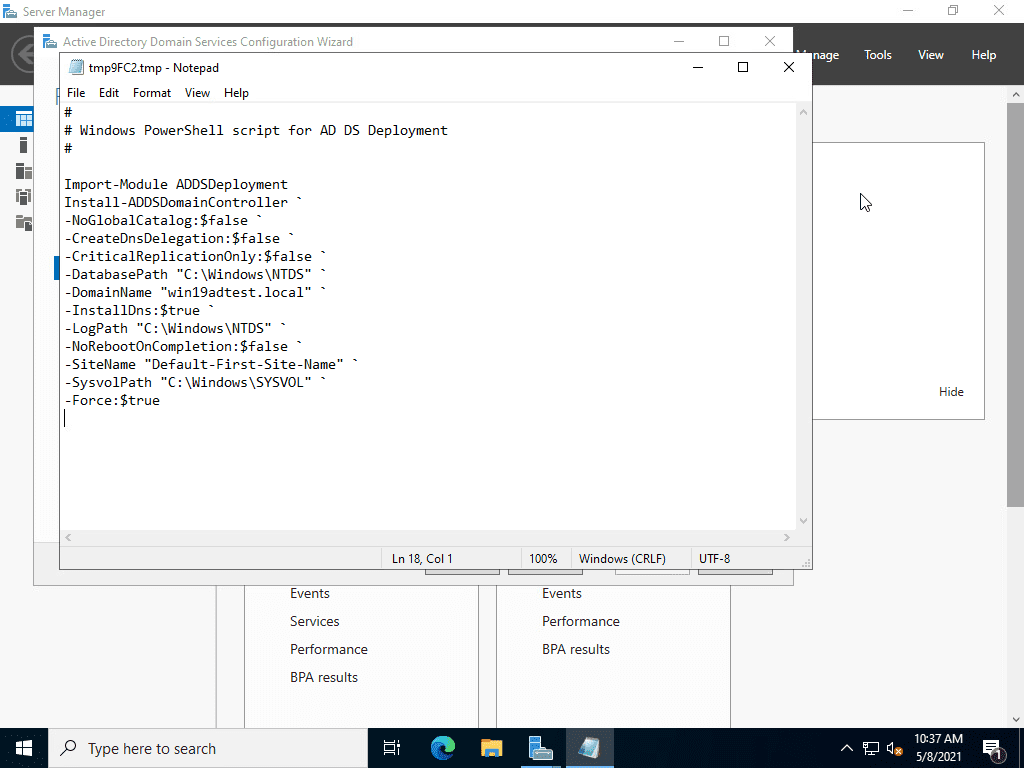
Here is a look at the PowerShell script to perform the ADDS configuration.
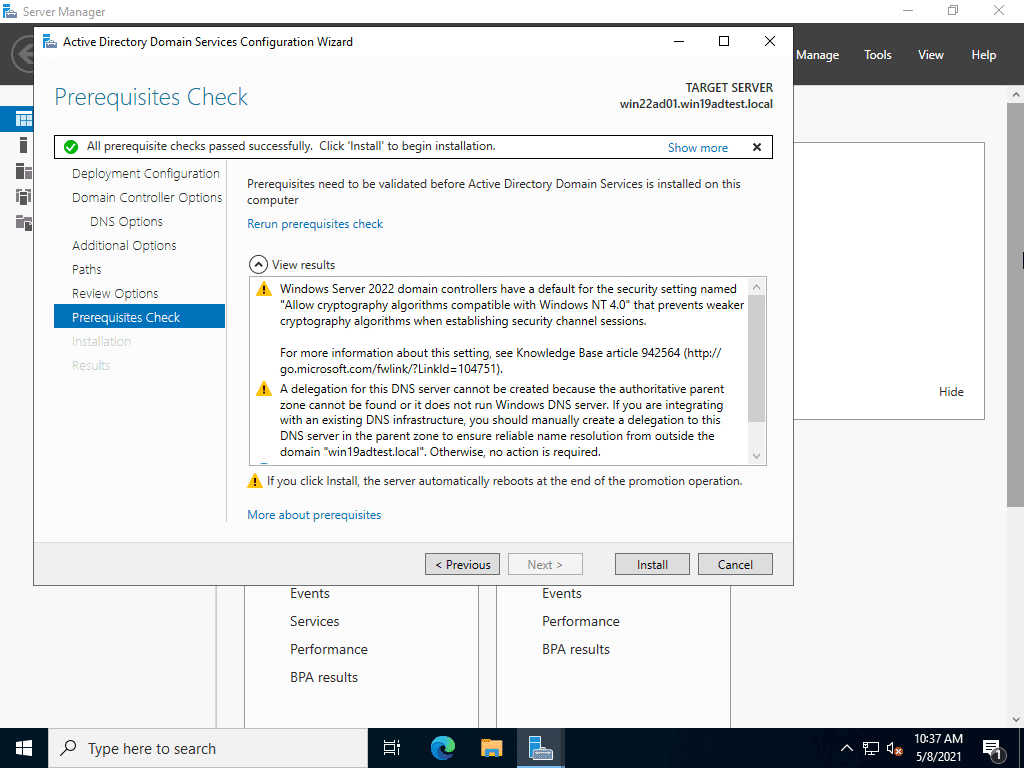
Running the prerequisite check. AS you will note, there is no schema upgrades or anything listed for Windows Server 2022. It appears the same schema is used as Windows Server 2016 Active Directory, the same as Windows Server 2019.
Transferring Active Directory roles from Windows Server 2019 to Windows Server 2022
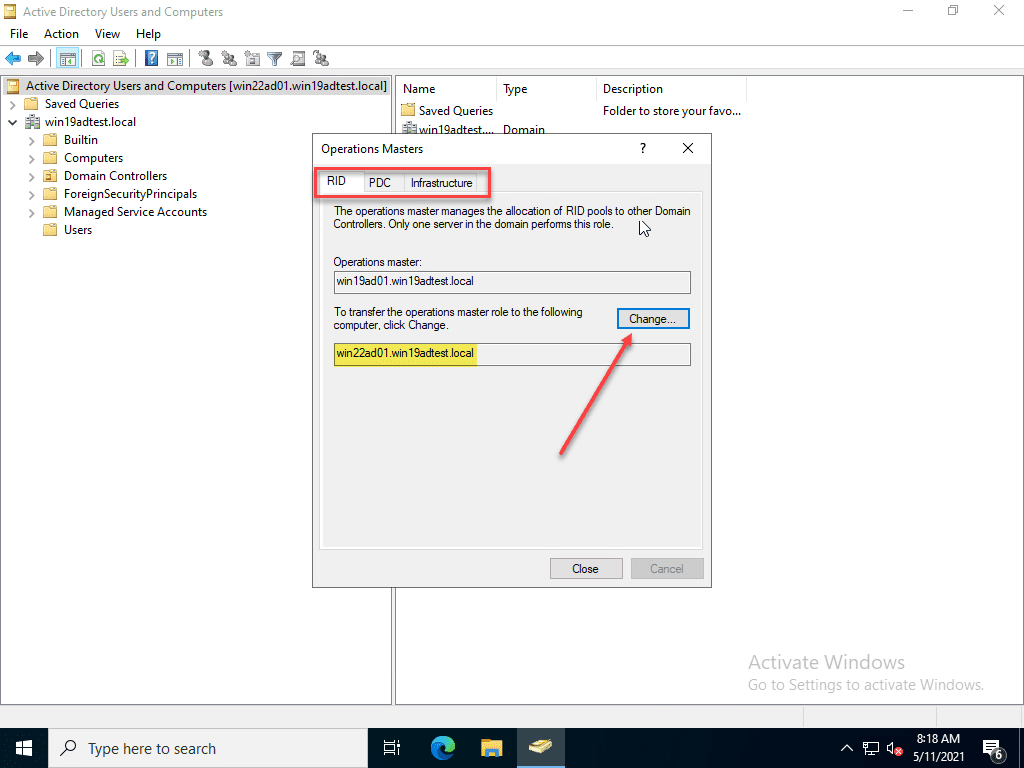
The steps below are familiar for most AD admins that have transferred roles before. But, just a quick run through of what this looks like with Windows Server 2022 – no difference. Transferring the RID, PDC, and Infrastructure Master roles below.
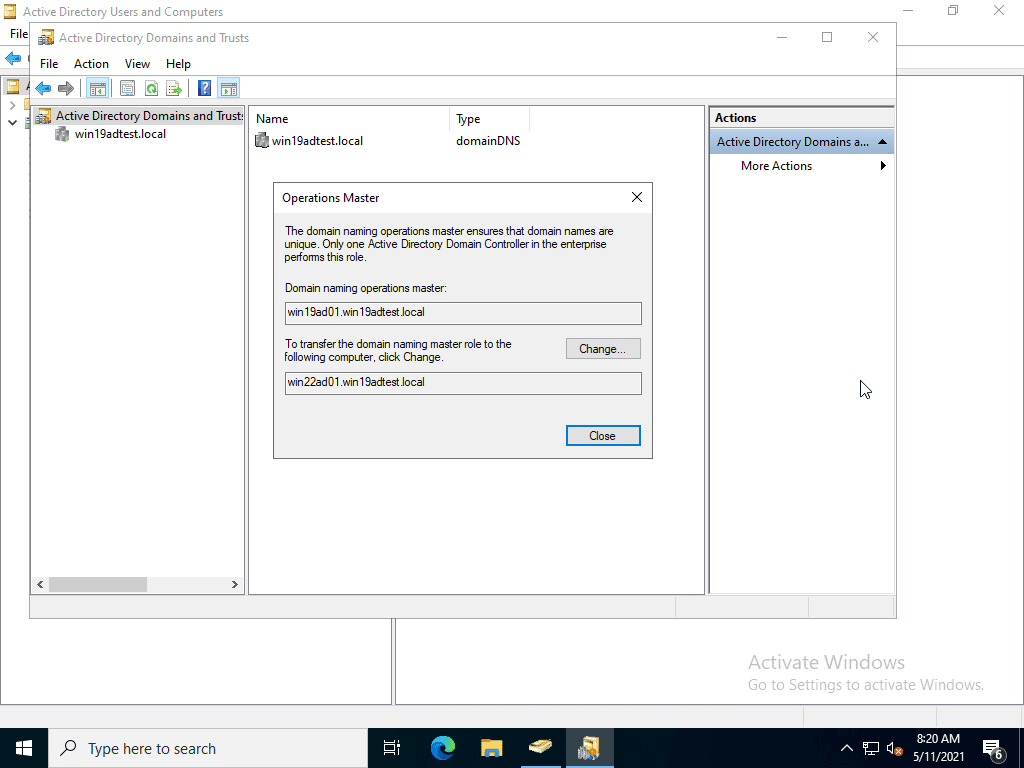
Transferring the domain naming master role to Windows Server 2022.
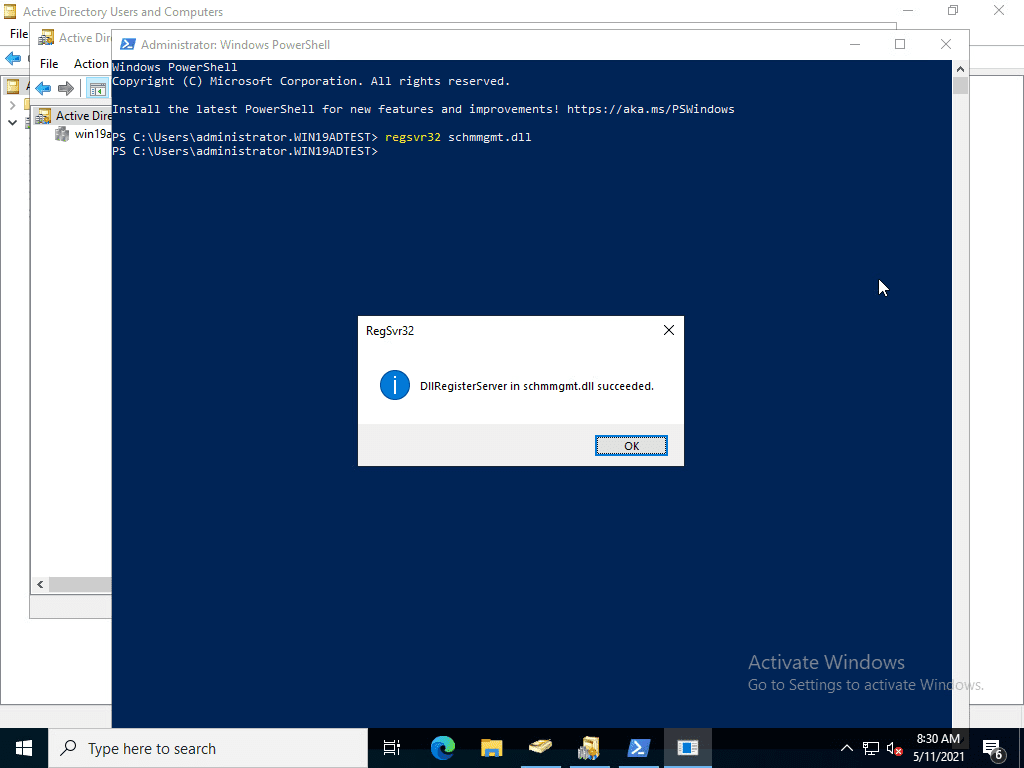
The same process of registering the Schema Management DLL must be performed for transferring the Schema Master role.
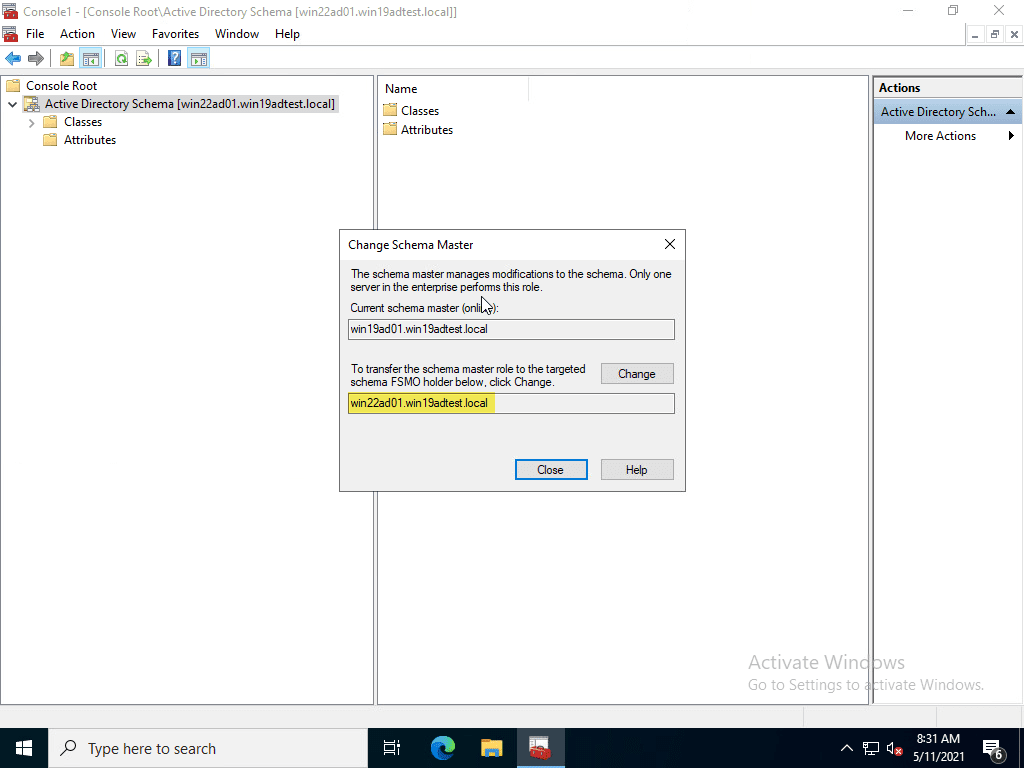
Transferring the Schema Master role.
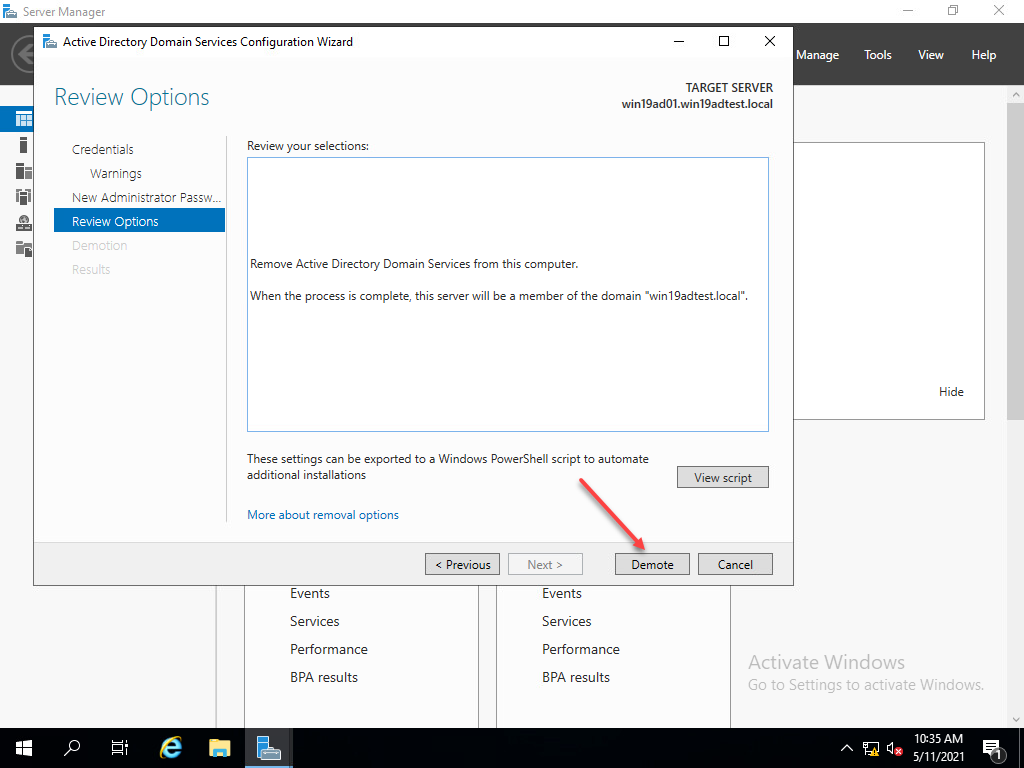
Demoting the Windows Server 2019 Domain Controller
After transferring the roles, I went through the process in Server Manager to demote the Windows Server 2019 domain controller.
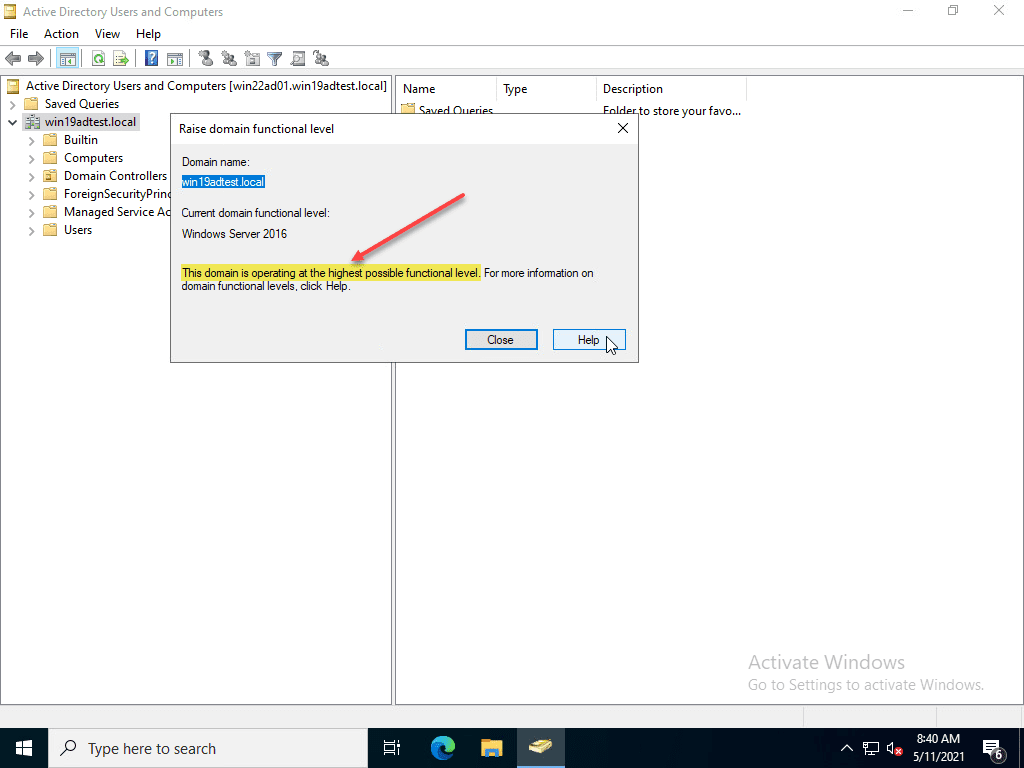
After demoting the Windows Server 2019 server, I wanted to check one last time on the Windows Server 2022 server which is now the solely available DC in the lab environment. It shows that Windows Server 2016 is the highest functional level.
Thoughts
Windows Server 2022 is a highly anticipated next release of the Windows Server operating system. It shows Microsoft’s shifting position on what features and functionality should be contained in Windows Server as well as the pivot to Azure integrated and cloud-native technologies.
As shown with the upgrade Windows Server 2019 Active Directory to Windows Server 2022 walkthrough, not much looks to have changed so far with Windows Server 2022 unless they sneak in features between the Insider Preview 20344 and the GA release. As shown, Windows Server 2016 is still the highest functional level for domains and forests at this time. Microsoft is drifting away from requiring Active Directory domain joins for most of their core features with each new Windows Server operating system release. This in itself shows where things are headed.


0 Comments