Virtual firewall vs Physical firewall in the home lab
So, in thinking about the direction of where my home lab is headed, I find myself using less and less discrete physical devices as opposed to running things as virtual machines. As a topic of interest for my home lab in 2022, I have toyed around with the idea of collapsing edge firewall services from a discrete firewall to a virtual machine running in the home virtualization cluster. In this virtual firewall vs physical firewall in the hoe lab post, I would like to hopefully stir up some discussions around what you guys are using as a firewall in the home lab, any thoughts you have, and what direction you might be headed with firewall services in the future.
Why virtual firewall vs physical firewall?
First, you may wonder, why consider a virtual firewall vs physical firewall in the home lab? For me, there are a few reasons that I am considering making the switch to virtual firewall services. These include the following:
- My home lab runs 24×7
- Physical firewalls are not cheap
- Better performance
- More disaster recovery options
- Another device to turn off for power consumption
- Integration with software-defined networking such as NSX-T
- Licensing is readily available through networking and other connections in the community
Let me detail how these reasons sway things towards a virtual firewall vs physical firewall and see if any of these reasons resonate with the community and what you are doing.
1. My home lab runs 24×7
In the case of my home lab, it already runs 24×7. If you don’t have virtual infrastructure that runs all the time, it may not be something you would consider as you would of course be shutting down your edge firewall with your home lab environment, potentially shutting down general Internet usage if you didn’t have another means for connecting to your ISP.
Since my home lab runs 24×7, folding the firewall into the home lab would make sense and allow taking advantage of the other capabilities of workloads that are virtual, as we will touch on a bit further.
2. Physical firewalls are not cheap
One thing you have probably noticed is that physical firewalls that have decent throughput, features, and performance are not cheap. When you start costing out enterprise firewalls that can do advanced threat protection and still provide performance to match today’s 1 gig Internet connections (and higher), these are insanely expensive.
3. Better performance
When I say better performance, I mean in respect to compared to the equivalent physical firewall. Virtual firewalls are generally less expensive since you are taking on the cost of the underlying physical hardware in your own virtualization environment. So for equivalent expense, your money generally goes further with virtual firewall appliances compared to a physical firewall.
4. More disaster recovery options
This point is a given for virtualized resources. When workloads are virtualized, you have many more options for protecting them than you do with physical hardware appliances. You can protect your virtual firewall the same way as any other virtual machine at that point by taking CBT-enabled snapshots as often as you would like.
It also enables replicating your VM firewall to another location, offsite copies, easily cloning for testing purposes, and many others. If you are considering a virtual firewall vs physical firewall, this is one of the major advantages of using virtual resources.
5. Another device to turn off for power consumption
If you are already running your home lab 24×7 like me, then running the virtual firewall inside a virtual machine is just another device you can power off and not have running consuming power. This just becomes part of the footprint of the existing virtual environment which is already running.
6. Integration with software-defined networking such as NSX-T
With virtual firewall appliances, there is also better integration with software-defined networking solutions like NSX-T. For example, Palo Alto’s VM-series firewalls and their integration with NSX-T is solid and deployment can be triggered from integration between NSX-T manager and Panorama.
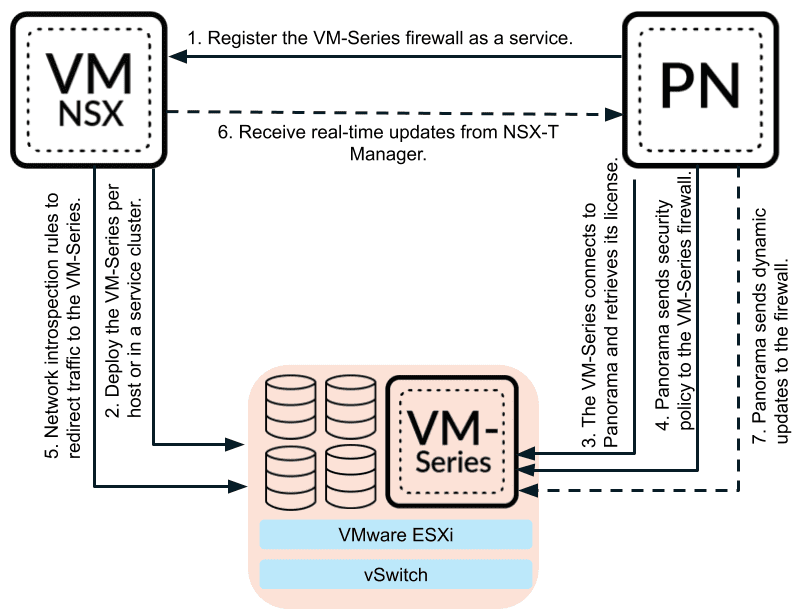
7. Licensing is readily available through networking and other connections in the community
When it comes to virtual firewalls, through vendor partners, communities, online/in-person events, vExpert program, and other great community-driven options, you can often get access to the bits for virtual firewalls and NFR keys.
Why not virtual firewall vs physical firewall?
Now, let’s discuss for a moment why you might not choose a virtual firewall vs physical firewall. These reasons might include:
- Your lab is not online 24×7 – Again, this one is fairly obvious. If the lab environment is not constantly available, running a virtual firewall may not be an option
- Your lab may not be highly available (more than one node in a cluster) – You may not want to run a virtual firewall if you are not configured with highly available storage and more than one node
- Your lab may be volatile and constantly in flux – If you are constantly building up and tearing down your lab environment, including hardware configurations, it is probably not a good idea
- You like the idea of having a discrete firewall outside of your virtual environment – Some prefer the idea, even with a highly available lab environment to run their firewall outside their virtual cluster.
Thoughts and opinions
What about you guys? What do you run inside your home lab environment – virtual firewall vs physical firewall? If you have a physical firewall, any plans on changing that soon? If you are running a virtual firewall, what variety are you running and why? Please post in the comments on what you are using in the home lab as it helps share the knowledge and experience often gained with the home lab “school of hard knocks.”


0 Comments