A great solution to run inside Kubernetes is Hashicorp Vault. Vault server is a solution from Hashicorp that allows you to securely introduce secrets management and inject secrets in your environment by using environment variables, dynamic API calls, etc. You can also configure and set up a Vault cluster in your environment for high availability for your secrets management. Vault is a great solution to spin up inside your Kubernetes cluster and run as a pod in your environment for managing secrets. You can maintain static and dynamic secrets using Vault and retrieve secrets for dynamic builds, etc. Let’s see how to install Hashcorp Vault in Kubernetes.
Vault Server
Vault secrets are stored securely in the Vault server using several means, such as key-value pairs. Using Vault, you can secure, store, and tightly control access to tokens, passwords, certificate authority data, encryption keys, and other sensitive data using the Vault UI, CLI, or using HTTP API REST calls to the Kubernetes API. Without permissions, users would receive an error making API request to receive credentials they do not have access to in the Kubernetes deployment.
Automation processes
Those who leverage Vault generally use it in automation processes, including Hashicorp Packer and Terraform, which can pull secrets from Vault during automated processes. The process to install Vault in Kubernetes using a Vault helm chart is straightforward.
After deploying using the Vault helm chart, running Vault agent containers is an efficient and easy way to host Vault in your organization. You can also use Vault to house Kubernetes secrets
Vault auth enable kubernetes
Using Vault, the Kubernetes auth method can authenticate with Vault using a Kubernetes service account token, easily introducing the Vault token into a Kubernetes pod running in a Kubernetes cluster. Vault Kubernetes authentication can also log in via JWT auth.
Vault features and use cases
Vault provides many great features, including:
Secrets management – You can centrally store and access secrets using the Vault server. Vault verifies access to a Vault secret across internal app instances, applications, systems, and infrastructure
Dynamic secrets – Vault can also generate on-demand and is unique to the client. Static and dynamic secrets are possible. The dynamic secrets can be created on the fly instead of spun up ahead of time.
Kubernetes secrets – You can use Vault and Kubernetes to securely inject secrets into your application stack after installing Vault with a helm chart.
Database credential rotation – Take the heavy lifting of manually rotating database credentials with Vault. You can instead automatically rotate database passwords in your Kubernetes deployment.
Automated PKI infrastructure – You can use Vault to create X.509 certificates on demand quickly
Identity-based access – You can use trusted identities to authenticate and access different clouds, systems, and endpoints. Using Vault Policy, you can enforce who gets access to what secrets
Data Encryption & Tokenization – You can keep your data secure in a centralized workflow for untrusted or partially trusted systems
Key management – Manage KMS keys in a standardized workflow
Highly available vault cluster – You can create a highly available vault cluster
Vault agent containers
Using Vault agent containers, you can inject secrets into Kubernetes pods. The applications can act as secret consumers of Vault and require the application to authenticate and acquire a client token, manage the token lifecycle, retrieve secrets, and managing secrets.
Vault agents
This introduces the requirement that deployments install and configure Vault agents along with the applications.
Vault secrets management
Vault provides robust secrets management, including secrets storage, dynamic secrets, Vault namespace, secure plugins, detailed audit logs, and lease and revoke secrets.
You can encrypt and store data in the storage backend of your choice with Vault. With Vault secrets, you can create dynamic secrets that are ephemeral and programmatically generated.
Install Vault in Kubernetes
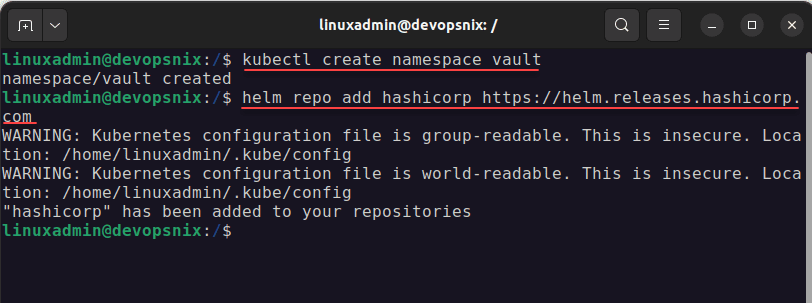
Let’s look at installing Vault in Kubernetes and see what steps are involved. First, let’s create a new namespace to house our Vault installation. We don’t want to create the Vault Server in our default namespace.
Creating the Vault namespace
kubectl create namespace vault
Next, after creating the vault namespace let’s add the helm chart repository for Vault:
helm repo add hashicorp https://helm.releases.hashicorp.comCommand to install Vault
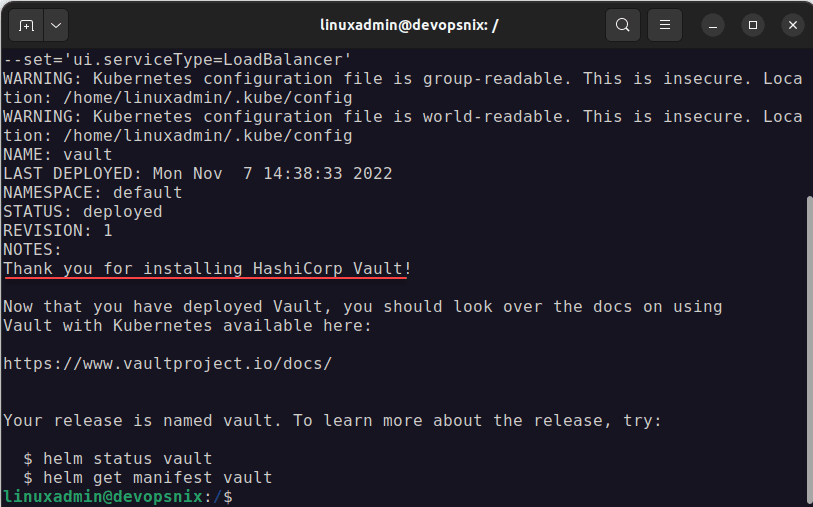
Next, we issue the command to install Vault, using the helm command with a couple of parameters:
helm install vault hashicorp/vault --set='ui.enabled=true' --set='ui.serviceType=LoadBalancer'The great thing about using the helm chart to install Vault server is that it sets up the service account, vault pods, vault statefulset, vault cli, service accounts, Vault internal app processes, Vault agent injector, service metadata, and vault data on our persistent storage, etc. There is no configuration file to update or customize.
You can also run git clone https to pull down the file to install via manifest as well.
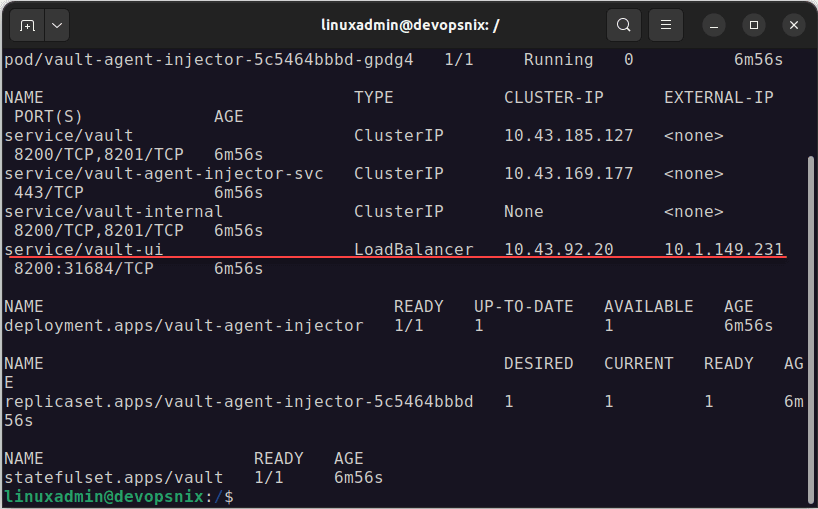
Checking the Vault pods
We can now look at the containers and see if they are running in the Kubernetes cluster using the command. This will show the Vault pod and containers running therein.
kubectl get pods -n vaultGetting Pod Metadata
You can look at the pod metadata with this command:
kubectl exec vault-0 env| grep vaultVault operator init
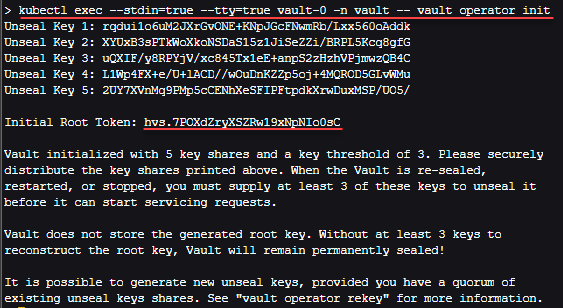
The next step, now that we have the containers running is the vault operator init process where we initialize our vault server to setup vault after running the Vault helm chart. To run Vault on Kubernetes and initialize the Vault Server, we need to run the command below.
Kubectl exec to run vault operator init
kubectl exec --stdin=true --tty=true vault-0 -n vault -- vault operator initThis will preset you with unseal vault secrets which essentially provide the master key to unseal the vault. You will also see your initial root token for your production setup. Be sure to record the root token and the unseal keys securely.
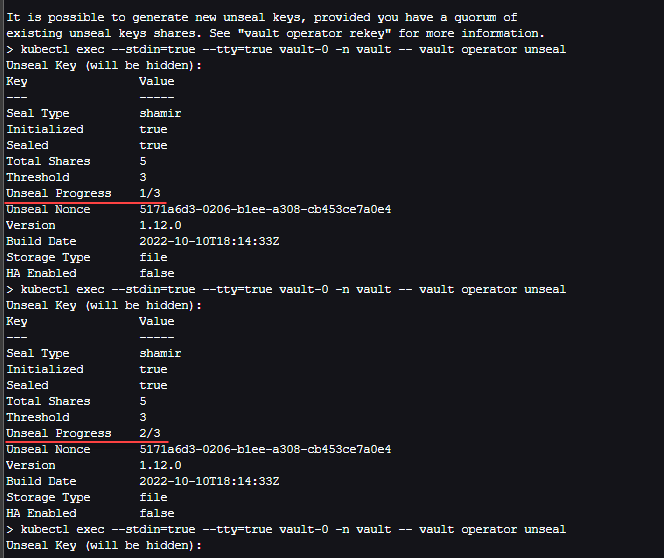
Vault unseal keys process
Next, we need to use the master keys to go through the unseal process, which has us paste in the unseal keys until the vault is unsealed.
Unseal the vault secrets
kubectl exec --stdin=true --tty=true vault-0 -n vault -- vault operator unsealRun this for the next three times and it will have you paste in the keys for Vault login.
Pods are in the running state
After you unseal the Vault, you can look at the pods and you should see these both in a running state with the pods ready. At this point, we can browse out to the Vault server on our Kubernetes clusters and
Getting the load balancer IP address for connectivity to the Vault UI
Finally, we can take a look at our LoadBalancer IP address to see which external IP address is exposed to our Vault UI. I am using MetalLB in my lab, so here I see the external IP address assigned to the Vault pod.
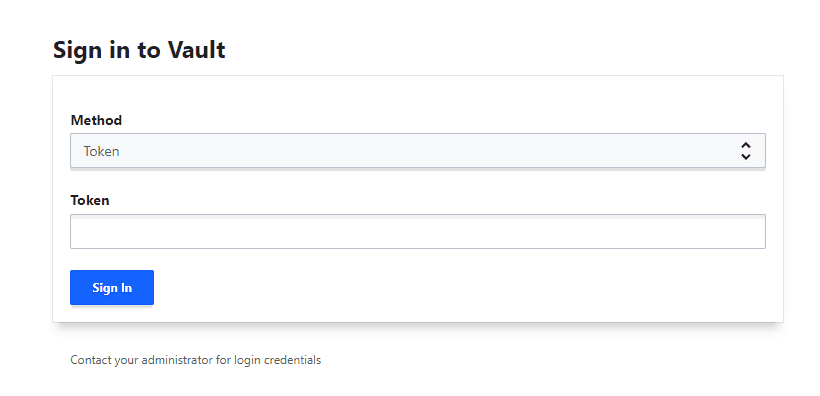
Logging into the Vault UI
The Vault auth mechanisms provide many different ways to authenticate to the solution
Using the UI or CLI, we can create the key-value store and secret path to house the sensitive information stored in the Vault Keystore. Once you login, you will see the default cubbyhole engine created for you. From this point, you can create new secrets engines, and entries in the engines to house your secrets.
Install Hashicorp Vault in Kubernetes FAQs
What is Hashicorp Vault? Hashicorp Vault is a robust secrets management solution that allows organizations to securely introduce secrets management in their environment and use sensitive information called programmatically from infrastructure as code solutions. Those who leverage vault have many capabilities such as PKI, dynamic secrets, rotating secrets, identity based access to secrets, and many other advantages.
What is Kubernetes? Kubernetes is a container orchestration solution allowing organizations to run containers at scale with availability, scheduling, disaster recovery, API access, and many other features that are not available when running plain containers on their own.
Why do you need to use a secrets engine for storing sensitive information? Storing secrets information in plain text or checking in secrets information in code is a bad practice and can lead to the potential for compromise. Organizations looking to bolster their cybersecurity posture, can benefit from introducing Vault server in their environment working with their Kubernetes cluster and other solutions.
What is helm? Help is a package management solution for Kubernetes. You can think of Helm like APT or YUM for installing packages. It makes the process to install new packages and applications in Kubernetes extremely easy.
Wrapping Up
Vault on Kubernetes is a great way to house the enterprise secrets management solution for your environment. I heavily use Vault for automated processes in my home lab environment, such as Packer builds, and Terraform code that requires connecting to systems using sensitive passwords. With Vault secrets, managing secrets in code or in the environment are super easy using the Vault client or programmatically.



0 Comments