As a follow-up to the news that Microsoft is rolling out a new Kerberos configuration change to remediate security vulnerability CVE-2021-42287. Starting with the rollout of the November 2021 security patches, Microsoft has introduced a new registry key that controls the behavior of your domain controllers until the July 12, 2021 patches are rolled out when the key will be eliminated. Until then, I have written a quick PowerShell script to check for the presence of the registry key and then set the value of the new registry key to the relevant value you want to configure. The key value affects how the domain controllers handle the PAC validation.
PacRequestorEnforcement registry key
Microsoft has created a specialized registry key to go along with the remediation for CVE-2021-42287 that controls how the new PAC security information is validated and enforced. The vulnerability involves the Kerberos Privilege Attribute Certificate (PAC) and allows potential attackers to impersonate domain controllers.
With the new process, Microsoft has added information to the PAC to validate the original requestor to validate they are who they say they are. The new registry key controls the action the domain controller takes in scrutinizing this new PAC information. Read the official information covering the registry key and Event Log entries here:
There are essentially three settings:
- Disabled – Represented by a 0 in the value for the PacRequestorEnforcement DWORD
- Deployment Mode – Represented by a 1 in the value for the PacRequestorEnforcement DWORD
- Enforcement Mode – Represented by a 2 in the value for the PacRequestorEnforcement DWORD
Microsoft does not recommend configuring the registry key with a 0 value for Disabled. They instead recommend using the 1 option. With the registry key set to 1, your domain controller will only log the missing PAC information in the SYSTEM log with new log entries for the new functionality. These will be logged as warnings as shown below:
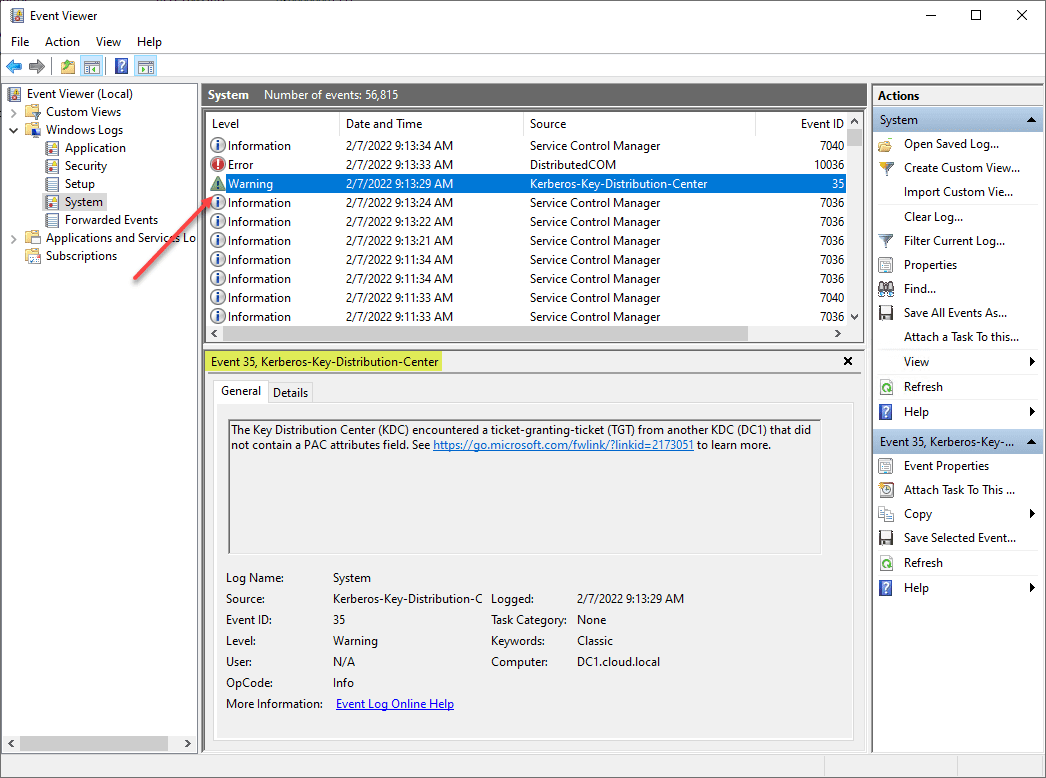
To control the behavior, you need to manually create the PacRequestorEnforcement DWORD manually and set the relevant configuration setting for your environment.
Create and Configure PacRequestorEnforcement Registry Key with PowerShell
The following PowerShell script checks for the presence of the DWORD and also configures the setting as a default to 1. The script does not allow setting the value to 0 as this is not recommended by Microsoft. If you rerun the script it will also allow changing the value from 1 to 2 and then from 2 to 1 if you want to go either direction.
You can clone the script from my Github repo here:
# Script to check for the existence of the PacRequestorEnforcement registry key and create it
# It will also allow changing the configured value to reflect the settings defined from Microsoft
# Disable - 0
# Deployment Mode - 1
# Enforcement Mode - 2
try {
Write-Host "Checking the registry for the presence of the PacRequestorEnforcement" -ForegroundColor Yellow
$regkeypath = 'HKLM:\SYSTEM\CurrentControlSet\Services\Kdc'
$valuename = 'PACRequestorEnforcement'
$check = (Get-ItemProperty $regkeypath).PSObject.Properties.Name -contains $valuename
if ($check -ne $null -and $check -ne 'true') {
try {
Write-Warning "Your Domain Controller does not have the PACRequestorEnforcement Registry Key. Would you like to add it and set value to 1?" -WarningAction Inquire
$Name = "PacRequestorEnforcement"
$value = "1"
New-ItemProperty -Path $regkeypath -Name $name -Value $value -PropertyType DWORD -Force | Out-Null
Write-Host "Your Domain Controller now has the PacRequestorEnforcement registry key" -ForegroundColor Green
}
catch {
Write-Host "You chose not to implement the PacRequestorEnforcement registry key" -ForegroundColor Red
}
}
else {
$pacvalue = (Get-ItemProperty -Path $regkeypath -Name $valuename).$valuename
Write-Host "Your Domain Controller already has the PacRequestorEnforcement DWORD and is set to $pacvalue" -ForegroundColor Green
if ($pacvalue -eq "2") {
Write-Warning "Your Domain Controller has the PacRequestorEnforcement DWORD set to 2. Would you like to set the value back to 1 for audit-only" -WarningAction Inquire
$Name = "PacRequestorEnforcement"
$value = "1"
New-ItemProperty -Path $regkeypath -Name $name -Value $value -PropertyType DWORD -Force | Out-Null
Write-Host "Your Domain Controller now has the PacRequestorEnforcement DWORD set to 1 - Deployment/Audit mode" -ForegroundColor Green
}
if ($pacvalue -eq "1") {
Write-Warning "Your Domain Controller has the PacRequestorEnforcement DWORD set to 1. Would you like to set the value to 2 for enforcement mode?. Make sure you are doing this consistently across your DCs." -WarningAction Inquire
$Name = "PacRequestorEnforcement"
$value = "2"
New-ItemProperty -Path $regkeypath -Name $name -Value $value -PropertyType DWORD -Force | Out-Null
Write-Host "Your Domain Controller now has the PacRequestorEnforcement DWORD set to 2 - Enforcement mode" -ForegroundColor Yellow
}
}
}
catch {
Write-Host "Error running the script" -ForegroundColor Red
}Wrapping Up
The new PacRequestorEnforcement registry key is the current way organizations can control the behavior of how domain controllers scrutinize and enforce the new PAC information added for remediating CVE-2021-42287. Using the script, you can create and configure PacRequestorEnforcement registry key with PowerShell to ensure it is introduced consistently and in an automated fashion.


0 Comments