
The world is moving towards cloud-native infrastructure, making infrastructure as code (IaC) a critical part of modern software development pipelines. As businesses increasingly use cloud-native infrastructure, compliance and security violations can emerge as challenges. This is where Terrascan, a comprehensive static code analyzer, comes into play to make sure infrastructure as code is secure and compliant.
What is Terrascan?
Terrascan, an open-source project by Tenable (from the acquisition of Accurics), is a static code analyzer designed specifically for Infrastructure as Code (IaC).
With the rise of cloud-native infrastructure, solutions like Terrascan have become increasingly important. It operates on the “shift left” principle, identifying potential security violations and compliance issues before the infrastructure is provisioned. By doing this, it enables developers to mitigate risk before provisioning cloud-native infrastructure.
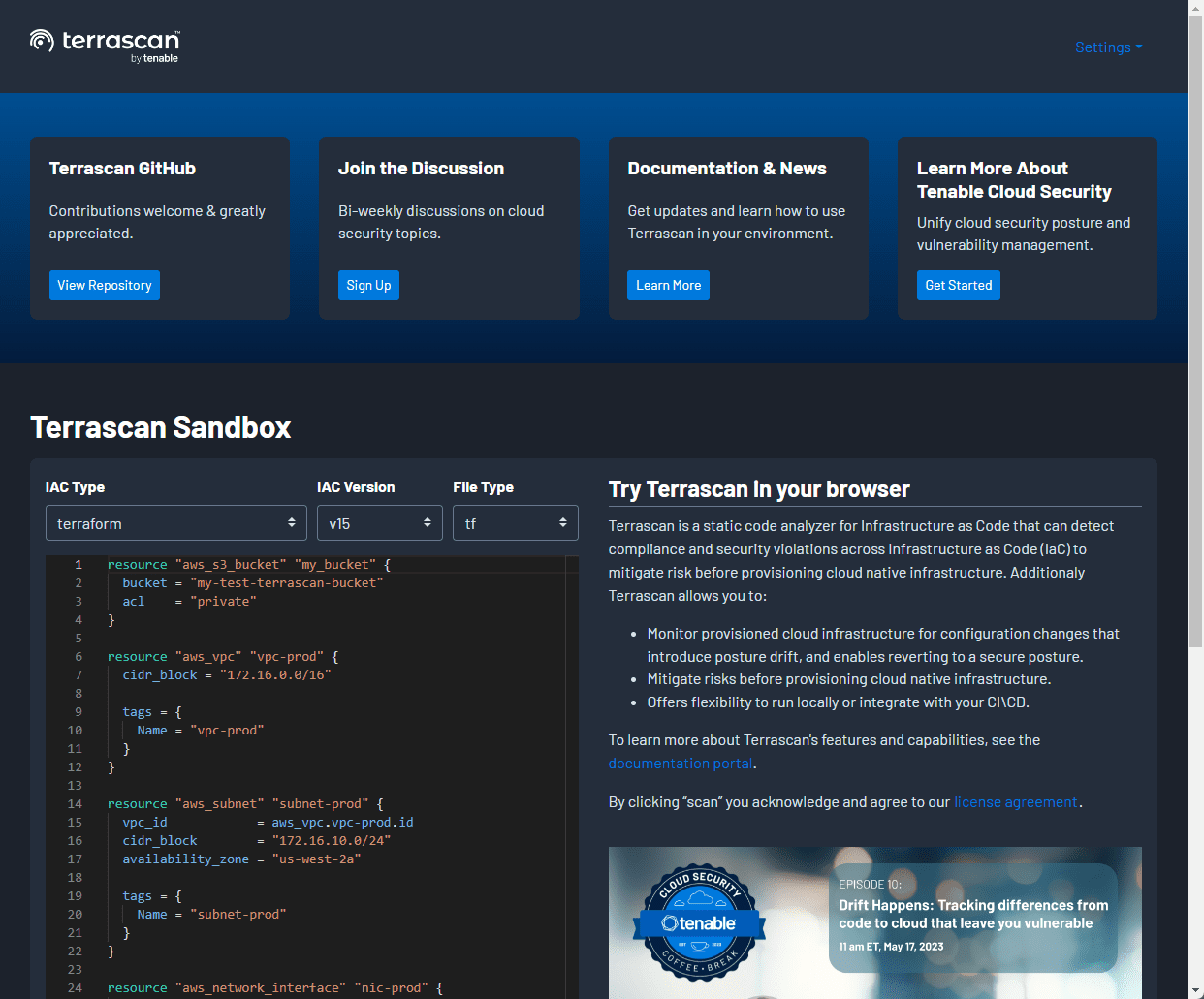
Cloud sandbox
You can try out the Terrascan cloud sandbox to get a feel for how the tool works and what the results look like. To visit the cloud sandbox, visit the URL here:
Terrascan’s Features and Capabilities
Terrascan has many features and capabilities, and what’s more, it’s easy to use. It supports popular IaC tools like Terraform, Kubernetes, Dockerfile, and more. It’s designed to detect compliance and security violations across infrastructure as code, helping maintain a secure posture for your provisioned cloud infrastructure.
It also has a rich set of built-in policies that follow security best practices. These are designed to detect common security violations across infrastructure, such as insecure configurations, and allow users to maintain a secure posture.
One of the key features is the ability to write custom policies. Custom policies enable users to enforce their specific compliance and security requirements. This is useful when you have unique security considerations that aren’t covered by the built-in policies.
In addition, it provides the following features:
Terrascan performs scans across your infrastructure as code (IaC) to identify misconfiguration
It allows continuously keeping an eye on your provisioned cloud infrastructure to spot configuration changes that may introduce posture drift while also enabling a quick return to a secure posture
It detects potential security vulnerabilities and compliance and security violations
It helps to mitigate risk before provisioning cloud-native infrastructure, ensuring a secure foundation from the start
Terrascan provides flexibility to run locally or integrate it within your CI/CD pipeline
Installing Terrascan and Setting Up a Terrascan Sandbox
To get started, you first need to install it. The installation process is simple and can be done either locally or in a containerized environment. Once installed, you might consider setting up a Terrascan sandbox. This is a safe environment where you can test and understand Terrascan’s features and capabilities without affecting your actual cloud infrastructure.
To install as a native exe:
curl -L "$(curl -s https://api.github.com/repos/tenable/terrascan/releases/latest | grep -o -E "https://.+?_Darwin_x86_64.tar.gz")" > terrascan.tar.gz
$ tar -xf terrascan.tar.gz terrascan && rm terrascan.tar.gz
$ install terrascan /usr/local/bin && rm terrascan
$ terrascanTo install via brew:
brew install terrascanWe will also look at installing it with a Docker container below.
Mitigating Risk and Maintaining a Secure Posture with Terrascan
Terrascan is designed to help mitigate risk before provisioning cloud-native infrastructure. Scanning your IaC configurations before deployment identifies potential security violations, enabling you to correct them before they become part of your live environment. This proactive approach helps to maintain a secure posture for your provisioned cloud infrastructure.
Terrascan also helps prevent ‘posture drift,’ which occurs when configuration changes introduce vulnerabilities into an otherwise secure environment. It does this by continuously monitoring provisioned cloud infrastructure, providing alerts whenever a compliance or security violation is detected.
Leveraging Continuous Monitoring and Remediation
Once your cloud-native infrastructure is provisioned, you can continue using Terrascan. It continues to monitor provisioned cloud infrastructure, ensuring that any security violations are quickly identified and mitigated as part of your CI/CD process.
When it detects a security violation, it alerts you and enables reverting to a secure state. By leveraging this capability, you can rapidly respond to any posture drift and ensure your provisioned cloud infrastructure remains secure.
Leveraging Terrascan to Detect Compliance
Terrascan can detect compliance and security violations before your code is deployed is one of Terrascan’s standout features. With Terrascan, you can ensure that your cloud-native infrastructure is provisioned following industry and company-specific security and compliance best practices. This helps to mitigate risks before provisioning resources.
How Terrascan Helps to Mitigate Risk in Cloud Native Infrastructure
It allows you to mitigate risk before provisioning cloud-native infrastructure. It does this by:
Evaluating your IaC scripts and identifying potential security violations and compliance issues before the infrastructure is provisioned
It helps in avoiding ‘posture drift.’ Posture drift happens when configuration changes introduce vulnerabilities into an otherwise secure environment.
It continuously monitors provisioned cloud infrastructure, helping identify and address these changes promptly, allowing you to maintain a secure posture.
Revert and Mitigate risks using Terrascan
Terrascan allows you to revert configuration changes that introduce security violations, enabling you to restore your security posture quickly. This combination of proactive risk mitigation and reactive remediation capabilities makes Terrascan an essential tool in provisioning secure cloud-native infrastructure.
Running Terrascan as a Docker container
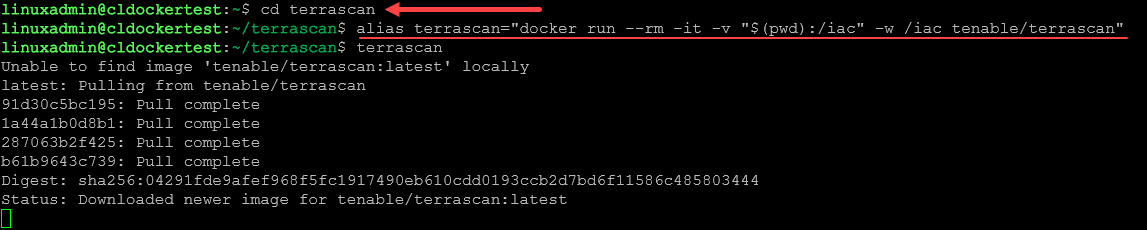
You can easily test out the solution by running it inside a Docker container by using the following to setup an alias to an interactive version of the terrascan container ran interactively.
As you can see below, we are setting up an alias to the docker run command, setting up a new container on the fly and running it interactively. The “$(pwd):/iac” directive tells terrascan to look at the current directory of focus from the shell command line for IaC code files like “.tf” files for Terraform.
$ alias terrascan="docker run --rm -it -v "$(pwd):/iac" -w /iac tenable/terrascan"I made a simple “terrascan” folder to run from, but you can run the command from anywhere as long as you have the alias configured. You just need to know where you are in the command line tree is where it will look for files.
On the first run of the terrascan command alias, we will see the Terrascan container pull down.
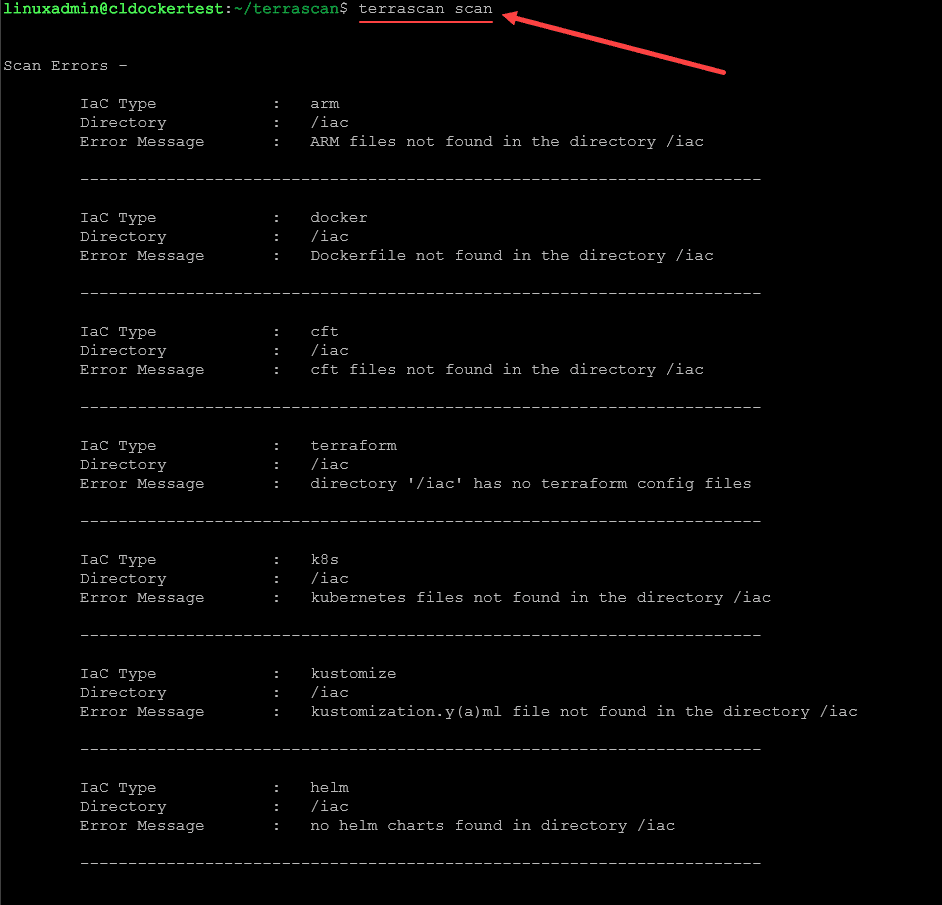
To run a scan, use the command:
terrascan scanWithout any files present, the command runs, but will note it didn’t find anything.
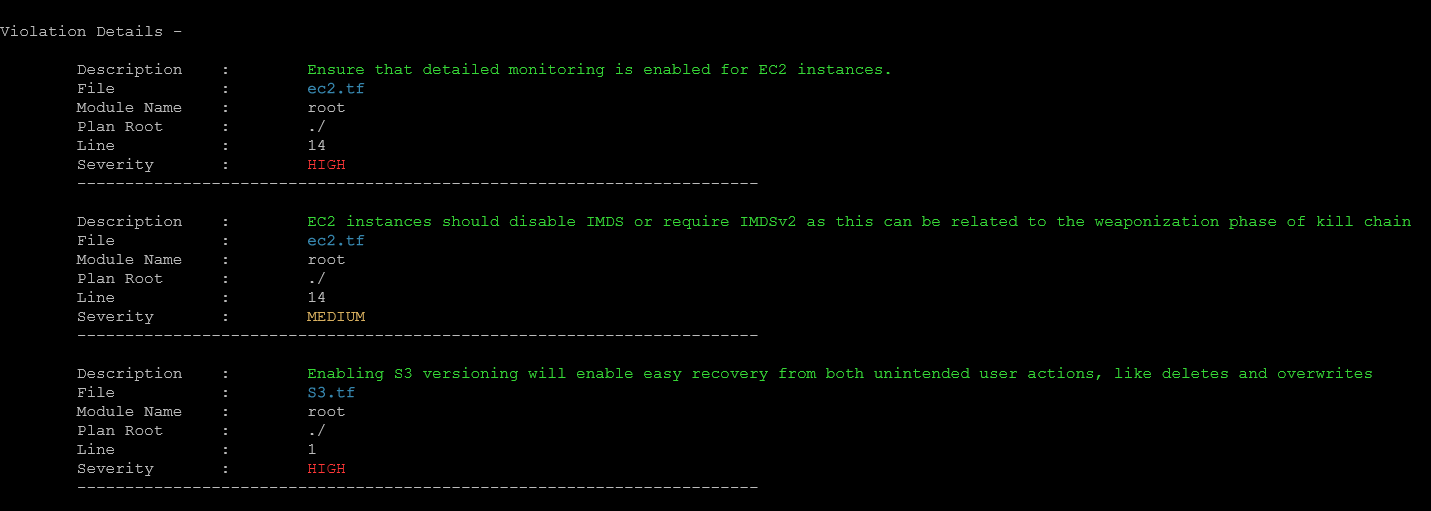
After adding some Terraform files to the directory where I am running terrascan scan command, we have files to work with and we can see it has findings that need to be addressed.
Frequently Asked Questions (FAQs) about Terrascan
1. What is Terrascan?
It is a static code analyzer designed to detect compliance and security violations in infrastructure as code (IaC). It is a vital tool for provisioning secure cloud-native infrastructure, enabling organizations to mitigate risks and maintain a secure posture before provisioning.
2. How does Terrascan detect security violations?
It evaluates your IaC configurations, highlighting potential security violations and compliance issues before the infrastructure is provisioned. By detecting these violations early, Terrascan helps maintain secure cloud-native infrastructure.
3. What is posture drift and how does Terrascan help?
Posture drift happens when configuration changes introduce vulnerabilities into a secure environment. Terrascan continuously monitors provisioned cloud infrastructure, promptly identifying and addressing these changes, enabling you to maintain a secure posture.
4. Can I create custom policies in Terrascan?
It allows you to create custom policies tailored to your specific requirements. These custom policies can be used to enforce unique security and compliance standards, enhancing the security of your cloud-native infrastructure.
5. How does Terrascan contribute to secure infrastructure provisioning?
Terrascan’s ability to detect compliance and security violations, mitigate risks before provisioning, and continuously monitor provisioned cloud infrastructure makes it an essential tool in secure infrastructure provisioning. It helps maintain a secure posture and avoid potential security violations across your infrastructure.
Wrapping up
As businesses continue to adopt Infrastructure as Code and cloud-native infrastructure, tools like Terrascan become more important. Terrascan can ensure your IaC is free from security violations before it’s provisioned, maintaining a secure posture and enabling continuous compliance. Whether you’re a novice or an experienced developer, Terrascan is a powerful tool in today’s infrastructure as code environments and cloud infrastructure.


0 Comments